What Does Rendered Services On Account Mean
Starting time published on TechNet on Sep 10, 2009
Group Managed Service Accounts superseded MSAs, which in Windows vii and Windows Server 2008 R2 (both no longer supported). Please utilise this updated link for more current information: https://docs.microsoft.com/en-us/windows-server/security/grouping-managed-service-accounts/grouping-manage...
==============================================
Ned hither over again. One of the more interesting new features of Windows Server 2008 R2 and Windows 7 is Managed Service Accounts. MSA's allow you to create an account in Active Directory that is tied to a specific computer. That account has its own circuitous password and is maintained automatically. This means that an MSA tin can run services on a computer in a secure and easy to maintain manner, while maintaining the adequacy to connect to network resources as a specific user principal.
Today I will:
- Describe how MSA works
- Explain how to implement MSA's
- Cover some limitations of MSA'southward
- Troubleshoot a few common issues with MSA's
Let's be nearly it.
How Managed Service Accounts Piece of work
The Windows Server 2008 R2 Advertizement Schema introduces a new object course chosen msDS-ManagedServiceAccount . Create an MSA, examine its objectClass attribute, and find the object has an interesting object class inheritance structure:
Estimator
msDS-ManagedServiceAccount
organizationalPerson
Top
User
The object is a user and a calculator at the same time, just like a computer account. Simply it does not have an object class of person like a computer account typically would; instead it has msDS-ManagedServiceAccount . MSA's inherit from a parent object grade of "Calculator", but they are also users. MSA objects do not contain new attributes from the Win2008 R2 schema update.
And this leads me to how MSA'southward handle passwords – it's pretty clever. An MSA is a quasi-figurer object that utilizes the same countersign update mechanism used by computer objects. Then, the MSA business relationship password is updated when the calculator updates its password ( every 30 days past default ). This can be controlled - but similar a reckoner's password - with the following two DWORD values:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesNetLogonParameters
DisablePasswordChange = [0 or 1, default if value proper noun does non exist is 0]
MaximumPasswordAge = [1-1,000,000 in days, default if value name does non exist is 30]
MSA's, like computers, exercise non observe domain or fine-grained countersign policies. MSA'southward use a circuitous, automatically generated countersign (240 bytes, which is 120 characters, and cryptographically random). MSA'southward cannot be locked out, and cannot perform interactive logons. Administrators tin can ready an MSA password to a known value, although at that place's ordinarily no justifiable reason (and they can be reset on demand; more on this later).
All Managed Service Accounts are created (by default) in the new CN=Managed Service Accounts, DC=<domain>, DC=<com> container. You lot can see this by configuring DSA.MSC to show "Avant-garde Features":


Equally yous will see later though, there isn't much point to looking at this in AD Users and Computers because… wait for it… all your assistants will be washed through PowerShell . Yous knew that was coming, didn't you?
MSA'south automatically maintain their Kerberos Service Principal Names (SPN), are linked to one computer at a time, and back up delegation. A network capture shows a correctly configured MSA using Kerberos:


Implementing MSA'southward
Wood and Os Requirements
To use MSAs you must:
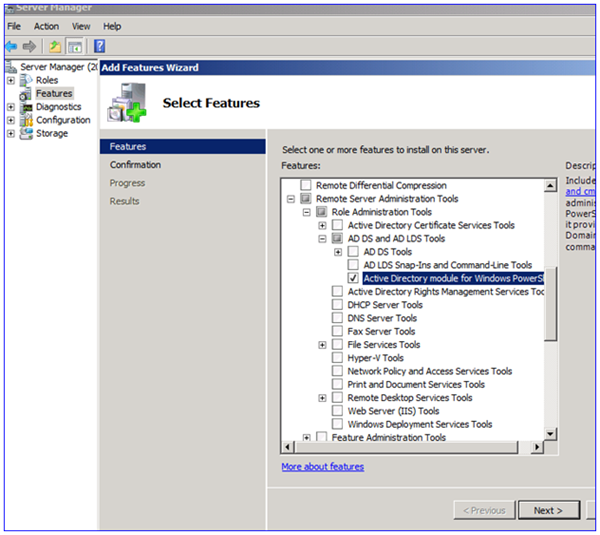
- Use Active Directory
- Extend your Ad schema to Windows Server 2008 R2
- Host services using MSAs on Windows Server 2008 R2 and Windows 7 computers (MSAs cannot be installed on down-level operating systems)
- PowerShell, AD PowerShell (part of the RSAT), and the .Internet 3.5x framework enabled on any computers using or configuring MSAs
MSAs do not crave a specific Forest Functional Level, but at that place is a scenario where part of MSA functionality requires a Windows Server 2008 Domain Functional Level. This means:
- If your domain is Windows Server 2008 R2 functional level, automatic passwords and SPN management will piece of work
- If your domain is less than WIndows Server 2008 R2 Domain Functional Level, automatic passwords will piece of work. Automatic SPN management will not work, and SPN'due south volition take to be maintained past administrators
Deployment
Using a new MSA always works in four steps:
1. You create the MSA in AD.two. You associate the MSA with a reckoner in AD.
3. You install the MSA on the calculator that was associated.
four. Yous configure the service(due south) to use the MSA.
Nosotros begin by using PowerShell to create the new MSA in Active Directory. You tin can run this command on Windows Server 2008 R2 or Windows seven computer that has the RSAT characteristic "Active Directory Module for Windows PowerShell" enabled. Perform all commands as an administrator.
i. Start PowerShell .2. Import the AD module with:
Import-Module ActiveDirectory
three. Create an MSA with:
New-ADServiceAccount -Proper noun <some new unique MSA business relationship proper name> -Enabled $truthful
4. Associate the new MSA with a target estimator in Active Directory:
Add together-ADComputerServiceAccount -Identity <the target computer that needs an MSA> -ServiceAccount <the new MSA yous created in footstep iii>
5. Now logon to the target computer where the MSA is going to be running. Ensure the following features are enabled:
- Active Directory Module for Windows PowerShell
- .NET Framework 3.5.1 Characteristic
6. Start PowerShell .
vii. Import the AD module with:
Import-Module ActiveDirectory
8. Install the MSA with:
Install-ADServiceAccount -Identity <the new MSA you created in stride 3>

Note: As well being a local ambassador on the computer, the business relationship installing the MSA needs to have permissions to modify the MSA in AD. If a domain admin this "just works"; otherwise, you would demand to delegate alter permissions to the service account's AD object.
ix. Now y'all can associate the new MSA with your service(s).
The GUI mode:
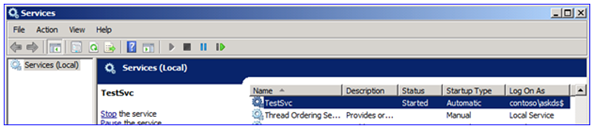
a. Start services.msc .
b. Edit your service properties.
c. On the Log On tab, set "This Account" to the domainname$ of your MSA. Then if your MSA was called "AskDS" in the "contoso.com" domain, it would exist:
contosoaskds$
d. Remove all data from Countersign and Confirm password – they should not contain whatever data:
e. Click Apply and Ok to the usual "Logon as a Service Right granted" message:
f. Start the service. It should run without errors.
The PowerShell way:
a. Showtime PowerShell .
b. Paste this sample script into a text file:
# Sample script for setting the MSA countersign through PowerShell
# Provided "As IS" with no warranties, and confers no rights.
# See http://www.microsoft.com/info/cpyright.mspx# Edit this section:
$MSA=" contosoaskds$ "
$ServiceName="' testsvc '"# Don't edit this section:
$Password=$nothing
$Service=Get-Wmiobject win32_service -filter "proper noun=$ServiceName"
$InParams = $Service.psbase.getMethodParameters("Change")
$InParams["StartName"] = $MSA
$InParams["StartPassword"] = $Password
$Service.invokeMethod("Change",$InParams,$null)c. Alter the highlighted red sections to correctly configure your MSA and service name.
d. Relieve the text file as MSA.ps1 .
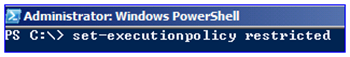
due east. In your PowerShell panel, become your script policy with:
Get-ExecutionPolicy
f. Set your execution policy to remote signing just:
Set up-ExecutionPolicy remotesigned
grand. Run the script:
h. Set your execution policy dorsum to whatsoever yous had returned in step E:
Note: Obviously, I made this case very manual; it could easily be automatic completely. That'due south the whole point of PowerShell after all. As well, it is ok to shake your fist at us for non having the User and Countersign capabilities in the V2 PowerShell cmdlet Set-Service . Grrr.
Removal
Removing an MSA is a simple 2-part process. At present that you know all the PowerShell rigmarole, here are the 2 things you practice:
1. Use the following PowerShell cmdlet to remove the MSA from a local reckoner:
Remove-ADServiceAccount –identity <your MSA proper noun>
two. Optionally, remove the service account from Active Directory. You lot can skip this step if you just desire to reassign an existing MSA from one figurer to another.
Remove-ADComputerServiceAccount –Identity <the computer the MSA was assigned to previously> -ServiceAccount <the MSA>
Group Memberships
The Gear up-ADServiceAccount and New-ADServiceAccount cmdlets practice not permit yous to brand MSA'due south members of groups. To do this you lot volition instead use DSA.MSC or Add-ADGroupMember .
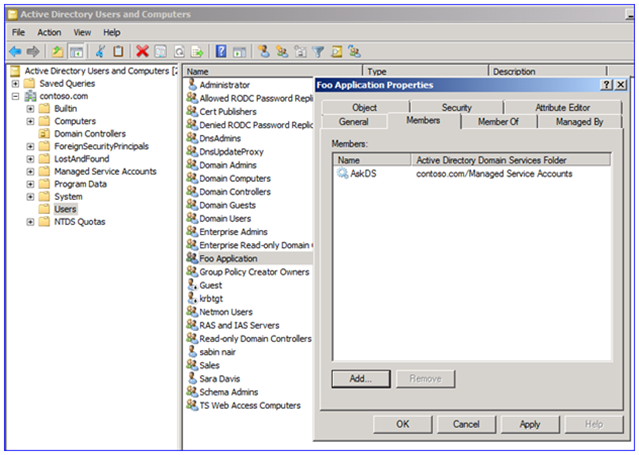
AD Users and Computers method:
1. Start DSA.MSC .
2. Select the group ( not the MSA).
three. Add together the MSA through the Members tab:
PowerShell method:
ane. Kickoff PowerShell .
2. Run:
Add-ADGroupMember "<your group>" "<DN of the MSA>"
And then for example:
Annotation : Employ the distinguished name of the MSA; otherwise Add-ADGroupMember will return "cannot discover object with identity". Don't try to utilise Internet GROUP as it doesn't know how to find MSA's.
Limitations
Managed Service Accounts are useful in nigh service scenarios. There are limits though, and understanding these up front volition save you planning time afterward.
- MSA'due south cannot span multiple computers – An MSA is tied to a specific calculator. It cannot be installed on more than ane reckoner at one time. In practical terms, this means MSAs cannot be used for:
- Cluster nodes
- Authenticated load-balancing using Kerberos for a group of web servers
The MSA can only be on one computer at a fourth dimension; therefore, MSAs are not compatible with cluster fail-over scenarios. And authentication through a load balancer would require you to provide a Kerberos SPN of the MSA business relationship-- that won't work either. Load balancing scenarios include Microsoft software-based and third-party hardware and software-based load balancing solutions. If y'all're clustering or NLB'ing, then you are still going to demand to use old fashioned service accounts.
A fundamental clarification: Y'all can have multiple MSAs installed on a single computer. And then if y'all have an application that uses 5 services, information technology'due south perfectly alright to use one MSA on all five services or five different MSA's at once.
- The supportability of an MSA is determined by the component, non Windows – Just considering y'all can configure an MSA on a service doesn't mean that the folks who make that service support the configuration. So, if the SQL team hither says "we don't support MSA's on version X", that'due south it. You have to convince them to back up their products, not me :-). Some proficient places to start asking, as we get closer to the general availability of Windows Server 2008 R2 in October:
TechNet Forums - http://social.technet.microsoft.com/Forums
MSDN Forums - http://social.msdn.microsoft.com/Forums
SQL Back up Weblog - http://blogs.msdn.com/psssql/default.aspx
Exchange Blog - http://msexchangeteam.com/
SharePoint Blog - http://blogs.msdn.com/sharepoint/
Dynamics Blog - https://community.dynamics.com/blogs/
BizTalk Blog - http://blogs.msdn.com/biztalk_server_team_blog/
For the most part MSA's are straightforward and have easily understandable errors. There are a few bug that people seem to come across repeatedly though:
Error: Error 1069: The service did not start due to a logon failure.
Crusade: Typically caused past the MSA being disabled. Use Set-ADServiceAccount to enable your MSA.
Error: Indistinguishable Backlink. The service account 'AskDS2' has backlinks to calculator 'CN=2008R2-F-05,CN=Computers,DC=contoso,DC=com'. This add operation volition potentially disable service accounts installed on the other computer. Cannot install service business relationship. Mistake Message: 'Unknown fault (0xc000005a)
Cause: Y'all are trying to associate an MSA with a computer that is already used past another computer. The error notes the server (in this instance, 2008r2-f-05) currently using the MSA. Un-associate and uninstall the MSA from the former computer earlier using it on the new one.
Error: Add-ADComputerServiceAccount : The object could not exist found on the server.
Cause: Yous gave an wrong identity for the MSA and PowerShell cannot observe it. Either it's been deleted or you typed in the incorrect proper noun.
Mistake: Please enter a valid countersign.
Crusade: You lot did not remove the password information in the service'south Logon On properties when editing in services.msc . See the setup steps above.
Error: The account name is invalid or does not be, or the password is invalid for the account proper noun specified.
Cause: This is typically caused past not adding the "$" character to the end of the account proper name used in the Log On tab in the service's properties in services.msc. Also, this error is acquired by merely mistyping the proper name of the account or forgetting to add the advisable domain.
Concluding Notes and References
For further reading on Managed Service Accounts, check out:
- Service Accounts Pace-by-Step Guide
- Managed Service Accounts
And there you go – now go forth and tame your environs.
- Ned '120 characters ought to exist enough for anyone' Pyle
What Does Rendered Services On Account Mean,
Source: https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/managed-service-accounts-understanding-implementing-best/ba-p/397009
Posted by: moorejusbache.blogspot.com














0 Response to "What Does Rendered Services On Account Mean"
Post a Comment